@RevoluSecRevoluSec
Citizen Lab research into the use of commercial filtering products in countries under the rule of authoritarian regimes has uncovered a number of devices manufactured by U.S.-based Blue Coat Systems in Syria and Burma. Although Blue Coat has recently acknowledged the presence of their devices in Syria, this brief contributes to previous findings of devices in the country, documents additional devices in use in Syria, and identifies Blue Coat devices actively in use in Burma. This brief urges Blue Coat to investigate these claims and take action to prevent the further use of its technology in Syria and Burma.
Background
In recent months concern has grown over the use of commercial filtering technology in Syria, particularly in light of the Syrian regime’s violent crackdown against the 2011 uprising.1 Debate has recently focused on Blue Coat Systems, a California-based manufacturer of networking technology that develops network security and optimization tools. These tools include ProxySG devices that work with WebFilter, a product that categorizes billions of web pages to permit filtering of unwanted content.2 In August 2011, the website Reflets.info announced that it would be releasing a series of blog posts concerning the use of Blue Coat devices in Syria.3 Reflets.info later documented the presence of Blue Coat devices through in-country testing.4 This work was done in collaboration with the group Telecomix, which in October 2011 released 54gb of data purporting to be log files from Blue Coat devices active in Syria.5
Following the release of this information, Blue Coat initially denied that its equipment had been sold to Syria, a country to which the export or reexport of U.S. products is prohibited pursuant to U.S. sanctions (with certain limited exceptions).6 Media reports cited an unnamed Blue Coat representative who refuted the claim that the company had sold equipment to the Syrian government and stated that “under Blue Coat’s company policy, sales to countries subject to U.S. trade embargoes are not authorised.”7 Further reports quoted Blue Coat spokesperson Steve Schick as stating: “Blue Coat does not sell to Syria. We comply with U.S. export laws and we do not allow our partners to sell to embargoed countries.”8 It was also reported that the U.S. State Department was actively investigating the issue, with an unnamed official stating: “The issue of Blue Coat’s technology being used in Syria is one that the State Department is taking very seriously and is very concerned about.”9
However, on October 29, 2011, Blue Coat changed course and acknowledged the use of its technology in Syria. In a report in the Wall Street Journal, the company acknowledged that 13 of its devices, initially shipped through a distributor from Dubai and destined for the Iraqi Ministry of Communications, ended up in Syria.10 The company further acknowledged that the devices had been communicating with Blue Coat-controlled servers; however, the company claimed it does not monitor the locations from which such communications originate.11 Blue Coat senior vice president Steve Daheb stated: “We don’t want our products to be used by the government of Syria or any other country embargoed by the United States.”12
Since August 2011, Citizen Lab researchers have been conducting technical research into the presence of Blue Coat devices in Syria and in other countries under the rule of authoritarian regimes. While Blue Coat’s most recent admissions confirm a number of our findings, our research has also raised additional questions relevant to the use of Blue Coat technology for purposes that compromise internationally-recognized human rights. Our findings include the presence of additional Blue Coat devices active in Syria, as well as the presence of a number of Blue Coat devices in Burma. We urge Blue Coat to investigate these matters further in a transparent manner, and take action to prevent further use of Blue Coat technology in Syria and Burma.
Methodology
This report is a continuation of past OpenNet Initiative13 (ONI) research into the use of commercial filtering technologies to implement Internet censorship, particularly the sale of commercial technologies to Internet service providers (ISPs) in countries where government policy and practice is to restrict Internet content and violate human rights.14 The objective of this research was to document empirically and from an evidential basis that such technologies were and are in use in such countries, including Syria and Burma, and were and are actively being employed to censor Internet content.
Two methods were employed in conducting this research. In the case of Syria, all data was gathered remotely and no field research within the country was conducted. Evidence was gathered through network scans of publicly accessible servers in the IP address ranges of the Syrian Telecommunications Establishment. In the case of Burma, research was based on data gathered from in-country field testing and research. Testers within Burma ran ONI-developed software that tested access to 1,669 URLs, both within Burma and from a country that does not filter Internet content simultaneously. The data gathered from the country with no filtering is used as a control to compare the data from the country suspected of filtering. Two lists of URLs are tested: a ‘local’ list unique to each country and a ‘global’ list tested in all countries, which allows for comparisons across countries. The global list is comprised of internationally relevant websites with a range of content including political, social, conflict / security and Internet tools. The local list is designed individually for a specific country with URLs relevant to local politics and context. These lists are samples and are not meant to be exhaustive. The results of these tests are analyzed by ONI researchers to determine if a URL is blocked and how that block is occurring.15 The results obtained from this testing were combined with publicly available data gathered from technical analysis of Burmese networks and Blue Coat’s Site Review website to develop a fuller picture of Burma’s filtering regime.16
In the course of this project, we carefully deliberated on the ethics of our research methods.17 Issues raised included the ethics of accessing publicly available computer systems which, it is reasonable to believe, the administrators of such systems do not want outsiders to access. We concluded that as such systems were publicly available on the open Internet, the information gathered is fair grounds for research purposes. No attempts were made to subvert security measures, discover or use user credentials, or disrupt the operation of any computer system. Furthermore, no information disclosed here contains personally identifiable information.
The Citizen Lab contacted Blue Coat Systems on October 27, 2011, requesting more information regarding the sale and use of Blue Coat technology in countries against which U.S. trade sanctions are imposed. As of November 9, 2011, we have received no response.
Findings
While Blue Coat has acknowledged that 13 of their devices are present in Syria, there are additional aspects of this case that warrant further discussion and raise additional questions about the use of commercial filtering technologies in Syria and other countries under the rule of authoritarian regimes.
1. Additional Blue Coat devices present in Syria
Blue Coat has claimed that there are 13 of its devices present in Syria, which were part of a shipment of 14 devices reportedly sold to the Iraqi government.18 Additional information gathered by Citizen Lab researchers and other groups indicates, however, that there are more than 13 Blue Coat devices active in the country. The website Reflets.info, in collaboration with the Telecomix group, identified upwards of 15 Blue Coat devices actively in use in Syria.19 Separate from and additional to those devices identified by Reflets, Citizen Lab has identified Blue Coat devices active on four other IP addresses belonging to the Syrian Telecommunications Establishment, which are:
Blue Coat has claimed that there are 13 of its devices present in Syria, which were part of a shipment of 14 devices reportedly sold to the Iraqi government.18 Additional information gathered by Citizen Lab researchers and other groups indicates, however, that there are more than 13 Blue Coat devices active in the country. The website Reflets.info, in collaboration with the Telecomix group, identified upwards of 15 Blue Coat devices actively in use in Syria.19 Separate from and additional to those devices identified by Reflets, Citizen Lab has identified Blue Coat devices active on four other IP addresses belonging to the Syrian Telecommunications Establishment, which are:
- 213.178.244.100
- 213.178.244.173
- 213.178.244.174
- 213.178.244.175
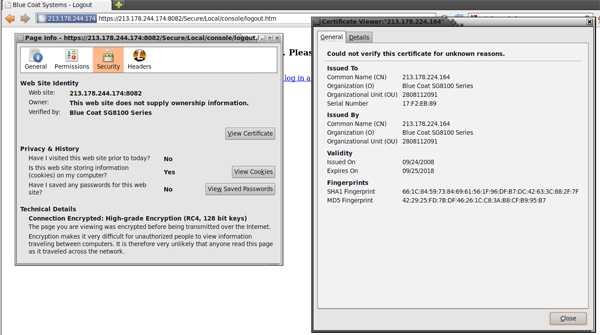
Citizen Lab identified these as Blue Coat devices through their web administration, security certificates and HTTP header data. Three of these have security certificates identifying them as Blue Coat SG8100 series devices (figure 1).
Figure 1: Blue Coat device on SCS IP address [213.178.244.174]